Step #1. Ensure Firewalld is running
The Firewalld package is preinstalled by default on AlmaLinux. First, check whether it is running or not. You can check the Firewalld service status using the following command:
sudo systemctl status firewalldIf the Firewalld service isn't running, the following output will be displayed:
]# sudo systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: inactive (dead)
Docs: man:firewalld(1)Now, start the Firewalld service using the following command:
sudo systemctl start firewalldAfter that, verify the status of the Firewalld service:
sudo systemctl status firewalldHere is the output:
]# sudo systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since Sat 2023-11-25 02:05:29 UTC; 2s ago
Docs: man:firewalld(1)
Main PID: 10017 (firewalld)
Tasks: 2 (limit: 11852)
Memory: 35.8M
CGroup: /system.slice/firewalld.service
└─10017 /usr/libexec/platform-python -s /usr/sbin/firewalld --nofork --nopid
Nov 25 02:05:29 ip-172-31-27-69.us-east-2.compute.internal systemd[1]: Starting firewalld - dynamic firewall daemon...
Nov 25 02:05:29 ip-172-31-27-69.us-east-2.compute.internal systemd[1]: Started firewalld - dynamic firewall daemon.Now, use the following command to list all services configured by Firewalld:
sudo firewall-cmd --list-allHere is the output:
]# sudo firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: cockpit dhcpv6-client ssh
ports:
protocols:
forward: no
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules: Step #2. Update the system
Before you proceed with Fail2Ban installation, ensure your system is up-to-date. To update your package lists and upgrade existing packages, use the following commands:
sudo dnf updateStep #3. Install EPEL
The Fail2Ban package is unavailable by default in the AlmaLinux default repo. As a result, you'll need to install it from the EPEL repository. You can install the EPEL repo using the following command:
sudo dnf install epel-releaseStep #4. Install Fail2Ban
After installing the EPEL repo, use the following command to install the Fail2Ban firewall and the fail2ban-firewalld package:
sudo dnf install fail2ban fail2ban-firewalldHere is the output:
]# sudo dnf install fail2ban fail2ban-firewalld Extra Packages for Enterprise Linux 8 - x86_64 27 MB/s | 16 MB 00:00 Last metadata expiration check: 0:00:06 ago on Sat 25 Nov 2023 02:07:48 AM UTC. Dependencies resolved. ============================================================================================================================================================================================================================================== Package Architecture Version Repository Size ============================================================================================================================================================================================================================================== Installing: fail2ban noarch 1.0.2-3.el8 epel 21 k fail2ban-firewalld noarch 1.0.2-3.el8 epel 21 k Installing dependencies: esmtp x86_64 1.2-15.el8 epel 57 k fail2ban-selinux noarch 1.0.2-3.el8 epel 41 k fail2ban-sendmail noarch 1.0.2-3.el8 epel 23 k fail2ban-server noarch 1.0.2-3.el8 epel 478 k libesmtp x86_64 1.0.6-18.el8 epel 70 k liblockfile x86_64 1.14-2.el8 baseos 31 k policycoreutils-python-utils noarch 2.9-24.el8 baseos 253 k python3-pip noarch 9.0.3-23.el8 appstream 19 k python3-setuptools noarch 39.2.0-7.el8 baseos 162 k python36 x86_64 3.6.8-38.module_el8.5.0+2569+5c5719bc appstream 18 k Enabling module streams: python36 3.6 Transaction Summary ============================================================================================================================================================================================================================================== Install 12 Packages Total download size: 1.2 M Installed size: 2.3 M Is this ok [y/N]: y Downloading Packages: (1/12): liblockfile-1.14-2.el8.x86_64.rpm 3.7 MB/s | 31 kB 00:00 (2/12): python3-pip-9.0.3-23.el8.noarch.rpm 3.5 MB/s | 19 kB 00:00 (3/12): python3-setuptools-39.2.0-7.el8.noarch.rpm 8.9 MB/s | 162 kB 00:00 (4/12): policycoreutils-python-utils-2.9-24.el8.noarch.rpm 11 MB/s | 253 kB 00:00 (5/12): python36-3.6.8-38.module_el8.5.0+2569+5c5719bc.x86_64.rpm 1.7 MB/s | 18 kB 00:00 (6/12): esmtp-1.2-15.el8.x86_64.rpm 980 kB/s | 57 kB 00:00 (7/12): fail2ban-selinux-1.0.2-3.el8.noarch.rpm 4.8 MB/s | 41 kB 00:00 (8/12): fail2ban-sendmail-1.0.2-3.el8.noarch.rpm 2.7 MB/s | 23 kB 00:00 (9/12): fail2ban-firewalld-1.0.2-3.el8.noarch.rpm 161 kB/s | 21 kB 00:00 (10/12): fail2ban-1.0.2-3.el8.noarch.rpm 138 kB/s | 21 kB 00:00 (11/12): libesmtp-1.0.6-18.el8.x86_64.rpm 3.0 MB/s | 70 kB 00:00 (12/12): fail2ban-server-1.0.2-3.el8.noarch.rpm 3.2 MB/s | 478 kB 00:00 ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Total 2.2 MB/s | 1.2 MB 00:00 Extra Packages for Enterprise Linux 8 - x86_64 1.6 MB/s | 1.6 kB 00:00 —--- —--- Installed: esmtp-1.2-15.el8.x86_64 fail2ban-1.0.2-3.el8.noarch fail2ban-firewalld-1.0.2-3.el8.noarch fail2ban-selinux-1.0.2-3.el8.noarch fail2ban-sendmail-1.0.2-3.el8.noarch fail2ban-server-1.0.2-3.el8.noarch libesmtp-1.0.6-18.el8.x86_64 liblockfile-1.14-2.el8.x86_64 policycoreutils-python-utils-2.9-24.el8.noarch python3-pip-9.0.3-23.el8.noarch python3-setuptools-39.2.0-7.el8.noarch python36-3.6.8-38.module_el8.5.0+2569+5c5719bc.x86_64 Complete!
Configuring Fail2ban to prevent Brutre Force Attack
After you have installed the Fail2ban, now it's time to set up and configure the Fail2ban.
All Fail2ban configuration is stored at the /etc/fail2ban directory. Below detailed Fail2ban configuration you must know:
- The configuration fail2ban.conf is the main configuration of Fail2ban.
- The configuration jail.conf is an example of the Fail2ban jail configuration.
- The directory action.d contains fail2ban actions settings such as mail settings and firewall settings.
- The directory jail.d contains additional configuration for fail2ban jail.
To start configuring Fail2ban, you will need to copy the default jail configuration jail.conf to jail.local using the following command.
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Now edit the configuration jail.local using nano editor.
sudo nano /etc/fail2ban/jail.local
For the ban settings, you can change the configuration as you need. In this example, the global bantime will be 10minutes, the findtime will be 10minutes, and the maxretry is up to 3times.
The bantime option is the time of IP address will be banned to access the server. The findtime option is the duration between the number of failures before the ban action. And the maxretry option is the number of failures for IP addresses to get banned.
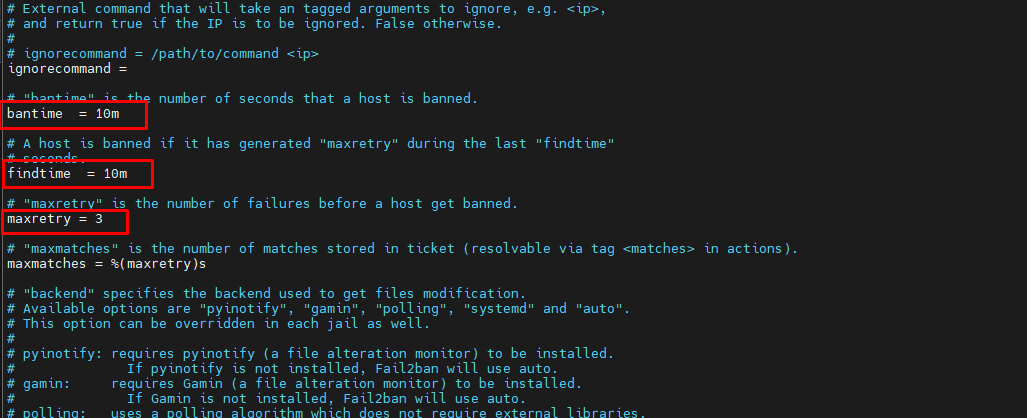
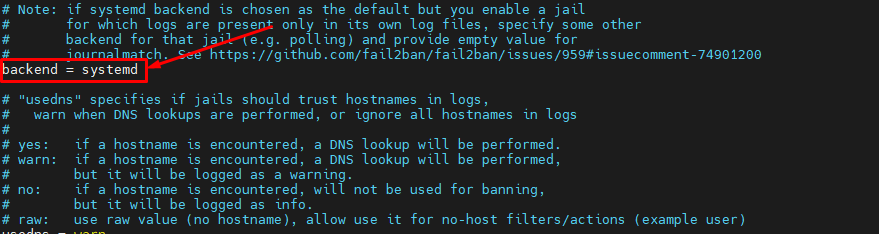
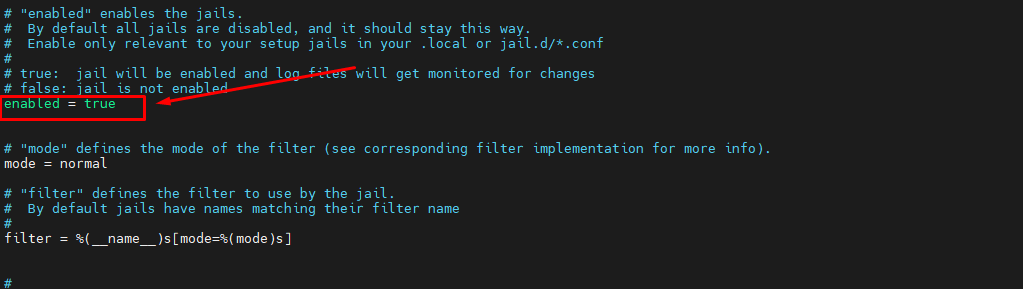
Furthermore please set backend = auto to backend = systemd and set jail enable = true in /etc/fail2ban/jail.local.
Using Fail2ban-client to Verify Fail2ban Status
The fail2ban provides a command-line fail2ban-client for interacting with the Fail2ban service. This allows you to manage and configure the Fail2ban from the command line, and also allows you to manage Fail2ban jails.
To verify fail2ban installation and configuration, run the fail2ban-client below command.
sudo fail2ban-client ping
If you get the output message such as "Server replied: pong", this means the Fail2ban is running without an error.
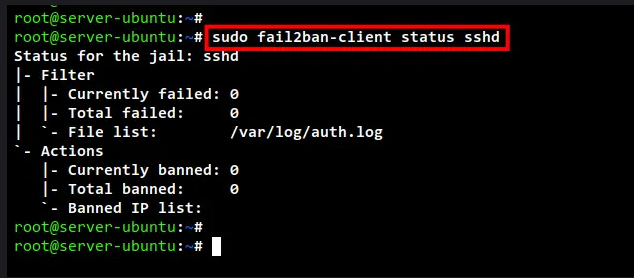
Next, run the fail2ban-client command below to check the status of sshd jail.
sudo fail2ban-client status sshd
Below you can see the detailed status of sshd jail. This includes the log file for the SSH service and the list of banned IP addresses on the sshd jail.
Now if you want to get a detailed configuration of the sshd jail, you can use the fail2ban-client command as below.
Check the bantime configuration for sshd jail. You will get the output of the bantime here in seconds.
Congratulation! You have now successfully installed and configured Fail2ban for securing Ubuntu 22.04.
Ban and Unban IP using Fail2ban-client
Another important thing about Fail2ban here is how to ban and unban IP addresses on Fail2ban. To do that, you can also use the fail2ban-client command.
To ban IP address manually on the sshd jail, you can use the fail2ban-client command below. Change the IP address with the IP address you want to ban.
sudo fail2ban-client set sshd banip IP-ADDRESS
To unban the IP address from sshd jail, you can use the fail2ban-client command below. Just be sure to change the IP address with the IP address you want to unban.
sudo fail2ban-client set sshd unbanip IP-ADDRESS
Now after you ban an IP address manually or unban an IP address, you can verify using the fail2ban-client command below.
sudo fail2ban-client status sshd
If you ban an IP address manually, make sure the IP address is available on the list of banned IP addresses. But if you unban an IP address, make sure the IP address disappears from the list of banned IP addresses.
Note: If you are using customize SSH port then you need to mention in jail.local file under [sshd] section like: port= {portnumber}

