You will learn how to install OpenVPN on a CentOS 7 server and connect to OpenVPN from a client computer in this knowledge base.
Step 1: Install OpenVPN
Run to update the CentOS repository and packages.:
yum update -y
2. The OpenVPN package is not available for download from the normal CentOS repositories.
OpenVPN is ultimately accessible from the EPEL (Extra Packages for Enterprise Linux) repository.
Run this command to make the EPEL repository available:
yum install epel-release -y
3. Update the repositories again:
yum update -y
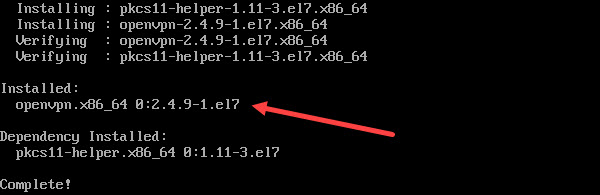
4. You can now install OpenVPN with the command:
yum install -y openvpn
Step 2: Install Easy RSA
The creation of a Public Key Infrastructure (PKI) is the next step. Installing simple RSA, a CLI tool for setting up and managing a PKI Certificate Authority (CA), is necessary to accomplish this.
To encrypt VPN connections, Easy RSA enables you to create SSL key pairs and a local certificate authority (CA).
You can use the wget command to download the simple RSA package. Install wget if it isn't already there on your CenOS system by running:
yum install -y wget
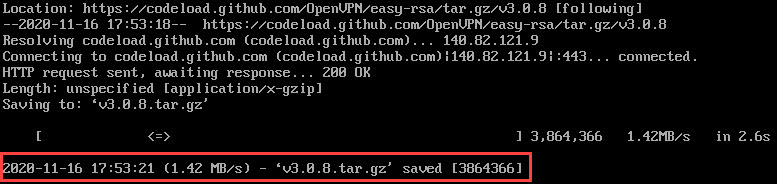
2.Run the below command.
wget https://github.com/OpenVPN/easy-rsa/archive/v3.0.8.tar.gz
3. Next, extract the downloaded archive:
tar -xf v3.0.8.tar.gz
4. Create and move into a new OpenVPN directory:
cd /etc/openvpn/
5. Then, create a subdirectoryeasy-rsaunder the path/etc/openvpn:
mkdir /etc/openvpn/easy-rsa
6. Move the extracted directory into /etc/openvpn/easy-rsa:
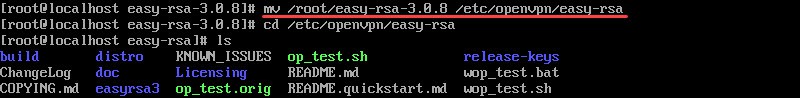
mv /root/easy-rsa-3.0.8 /etc/openvpn/easy-rsa
To check whether you have successfully moved everything from the easy-rsa-3.0.8 directory,
move into easy-rsa withcd /etc/openvpn/easy-rsaand list the content withls.
You should see a list of files and folders, as in the image below.
Step 3: Configure OpenVPN
After Easy RSA and OpenVPN have been installed, you may proceed to setting up the OpenVPN server.
You can set up the fundamental settings using the instructions in this section. It can be changed to suit your needs.
Be sure to return to the root directory before executing any of the instructions. To do this, enter the command cd in the terminal window.
- The first step is to copy the sample server.conf file from OpenVPN’s documentation directory:
cp /usr/share/doc/openvpn-2.4.9/sample/sample-config-files/server.conf /etc/openvpn
If you cannot find the OpenVPN sample configuration file, search for its location using thefindcommand:
find / -name server.conf
2. Then, open the copied configuration file with a text editor of your choice:
vi etc/openvpn/server.conf
The command opens the sample OpenVPN config file. The comments in the file begin with a hashtag # or a semicolon;.
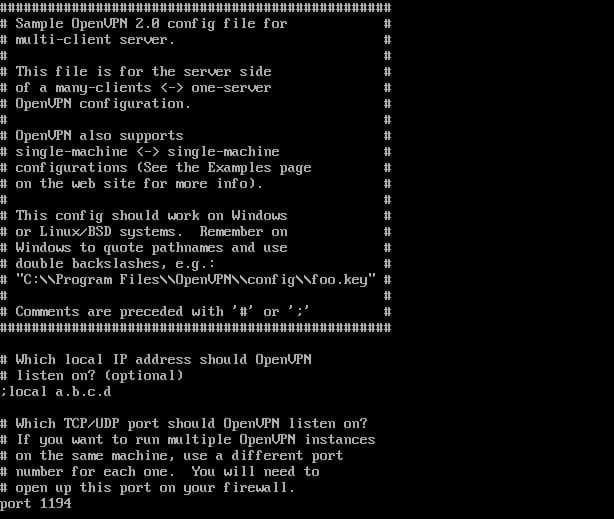
3. To set up the basic configuration, you need to uncomment the following lines by removing the semicolons.
topology subnet(makes the OpenVPN installation function as a subnetwork)push "redirect-gateway def1 bypass-dhcp"(instructs the client to redirect traffic through the OpenVPN server)push "dhcp-option DNS 208.67.222.222"(uses an OpenDNS resolver to connect to OpenVPN)push "dhcp-option DNS 208.67.220.220"(uses an OpenDNS resolver to connect to OpenVPN)user nobody(runs OpenVPN with no privileges)group nobody(runs OpenVPN with no privileges)
4. To enable TLS authentication, create a static encryption key next.
To do that, locate the line tls-auth ta.key 0 and comment it by adding ; in front of it. Then, add a new line under it:
tls-crypt myvpn.tlsauth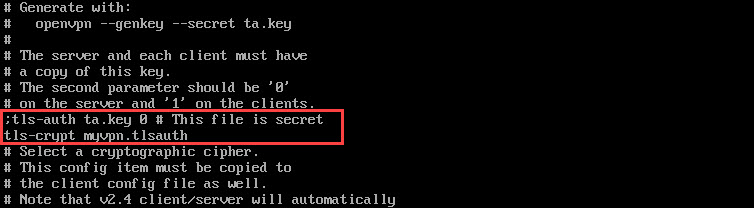
Note: The DNS servers to use when connecting to OpenVPN are specified in the configuration file. It is set to utilise OpenDNS resolvers by default, so that is how we left it. Alternatively, you can change it to different DNS resolvers by modifying the push "dhcp-option DNS 208.67.222.222" and push "dhcp-option DNS 208.67.220.220" lines.
5. Save and exit the configuration file.
6. Finally, generate the static encryption key specified in the file with the command:
openvpn --genkey --secret /etc/openvpn/myvpn.tlsauth
Step 4: Generate Keys and Certificates
- Create a vars configuration file using vars. example stored in the /easy-rsa/easyrsa3 directory. Move into the mentioned directory with:
cd /etc/openvpn/easy-rsa/easyrsa3
2. You can list the contents using thelscommand to check whether you have the vars.example file.
3. Copy the sample file vars.example under the name vars:
cp vars.example vars
If you list the files in the directory again, you should have a separate vars file that you can use to configure Easy RSA.
4. Open the vars file in a text editor of your choice:
vi vars
5. Scroll through the file and find the lines listed below.
#set_var EASYRSA_REQ_COUNTRY "US" #set_var EASYRSA_REQ_PROVINCE "California" #set_var EASYRSA_REQ_CITY "San Francisco" #set_var EASYRSA_REQ_ORG "Copyleft Certificate Co" #set_var EASYRSA_REQ_EMAIL "[email protected]" #set_var EASYRSA_REQ_OU "My Organizational Unit"
6. Uncomment the lines by removing#and replacing the default values with your information.
7. Then, find the line specifying the KEY_NAME and change it to "server":
export KEY_NAME="server"
8. Finally, change KEY_CN to the domain or subdomain that resolves to your server.
export KEY_CN=openvpn.yourdomain.com
9. Save and close the file.
10. Clean up any previous keys and generate the certificate authority:
./easyrsa clean-all11. Now, you can move on to building the certificate authority with thebuild-cascript. Run the command:
./easyrsa build-ca
You will be asked to set a CA Key Passphrase and a common name for your CA.
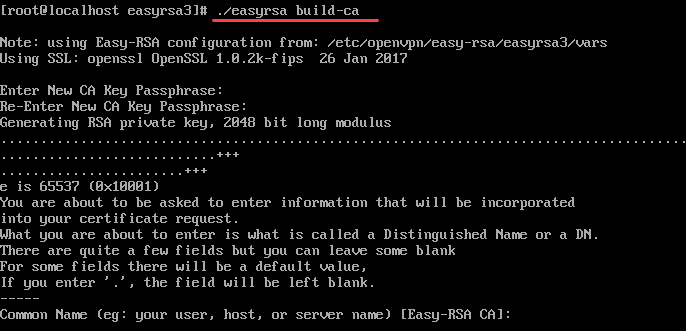
Note: To skip password authentication each time you sign your certificates, you can use the ./easyrsa build-ca nopass command.
12. Create a key and certificate for the server:
./easyrsa build-server-full server
13. Next, generate a Diffie-Hellman key exchange file by running:
./easyrsa gen-dh
14. For every client, you also need a certificate. Make a copy of them on the client machine after creating them on the server.
With the following command, we create a certificate and key for client1. You can modify the command by using a name of your choice.
./easyrsa build-client-full client1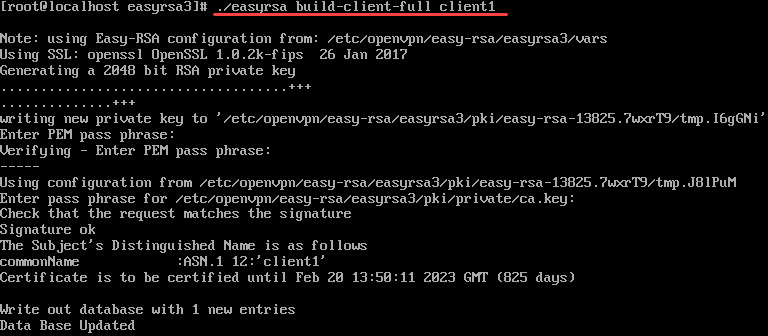
15. Once you have generated the keys and certificates, copy them from pki into the openvpn directory. To do so, navigate to the pki directory by running:
cd /etc/openvpn/easy-rsa/easyrsa3/pki
You need to copy four files in total:
- ca.crt
- dh.pem
- ca.key
- server.key
The first two files (ca.crt and dh.pem) are stored in the pki directory, while ca.key and server.key are in a subdirectory pki/private.
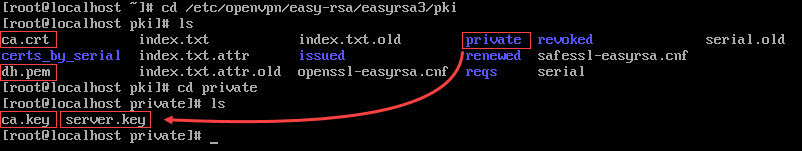
Therefore, copy ca.crt and dh.pem into the OpenVPN directory first:
cp ca.crt dh.pem /etc/openvpn
Then, move into the subdirectory private, and copy ca.key and server.key by running:
cd private
cp ca.key server.key/etc/openvpn
Step 5: Firewall and Routing Configuration
Set Firewall Rules
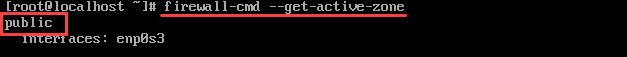
- Start by checking your active firewall zone:
firewall-cmd --get-active-zones
The output will show your firewalld zone. In the example below, it is public.
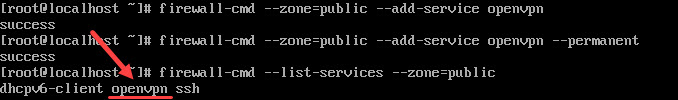
2. Add the openvpn service to the list of services firewalld allows within the active zone. The active zone in our example is public. If your active zone is trusted, modify the command accordingly.
firewall-cmd --zone=public --add-service openvpn
3. Next, make the settings above permanent by running the command:
firewall-cmd --zone=public --add-service openvpn --permanent
4. To check whether the openvpn service was added use:
firewall-cmd --list-services --zone=public
5. Then, add a masquerade to the runtime instance:
firewall-cmd --add-masquerade
6. And make it permanent:
firewall-cmd --add-masquerade --permanent
7. Verify the masquerade was added by running:
firewall-cmd --query-masquerade
The output should respond withyes.
Routing the Configuration
Routing to your OpenVPN subnet should be done once you have finished the previous steps.
- Create a variable that represents the primary network interface used by your server. In the command below, the variable is named
VAR. However, you can create a variable under the name of your choice.
VAR=$(ip route get 208.67.222.222 | awk 'NR==1 {print $(NF-2)}')
2. Next, permanently add the routing rule using the variable created above:
firewall-cmd --permanent --direct --passthrough ipv4 -t nat -A POSTROUTING -s 10.8.0.0/24 -o $VAR -j MASQUERADE
3. Reload firewalld for the changes to take place:
firewall-cmd --reload
4. Move on to routing all web traffic from the client to the server’s IP address by enabling IP forwarding. Open the sysctl.conf file:
vi /etc/sysctl.conf
5. Add the following line at the top of the file:
net.ipv4.ip_forward = 1
6. Finally, restart the service:
systemctl restart network.service
Step 6: Start OpenVPN
- To start the OpenVPN service, run the command:
systemctl -f start [email protected]
2. Then, enable it to start up at boot by running:
systemctl -f enable [email protected]
3. Verify the service is active with:
systemctl status [email protected]
The output should respond that the OpenVPN service for the server is active (running).
Step 7: Configure a OpenVPN Client
Once the OpenVPN server is configured, you can configure your client computer and connect to the server.
As mentioned in Step 4, each client machine needs to have local copies of the CA certificate, client key, SSL certificate, and the encryption key.
- Find and copy the following files from the server to the client machine:
- /etc/openvpn/easy-rsa/easyrsa3/pki/ca.crt
- /etc/openvpn/easy-rsa/easyrsa3/pki/client.crt
- /etc/openvpn/easy-rsa/easyrsa3/pki/private/client.key
- /etc/openvpn/myvpn.tlsauth
2. Then, create a configuration file for the OpenVPN client under the name client.ovpn on the client machine:
vi client.ovpn
3. Add the following content to the file:
client tls-client ca /path/to/ca.crt cert /path/to/client.crt key /path/to/client.key tls-crypt /path/to/myvpn.tlsauth remote-cert-eku "TLS Web Client Authentication" proto udp remote your_server_ip 1194 udp dev tun topology subnet pull user nobody group nobody
Make sure to replace the bolded parts with your respected values.
4. Save and close the file.
Step 8: Connect a Client to OpenVPN
The instructions on how to connect to OpenVPN differ depending on your client machine’s operating system.
For Linux Users
To connect to OpenVPN, run the command:
openvpn --config /path/to/client.ovpn
For Windows Users
- First, copy the client.ovpn configuration file in the C:Program FilesOpenVPNconfig directory.
2. Download and set up the OpenVPN software. The OpenVPN Community Downloads website has the most recent build available for download. OpenVPN should be launched when the programme has been installed.
3. Right-click the OpenVPN system tray icon and select Connect. To perform this task, you need administrative privileges.
For macOS Users
You can connect to OpenVPN from a macOS system using Tunnelblick (an open-source graphic user interface for OpenVPN on OS X and macOS).
Before launching Tunnelblick, make sure to store the client.ovpn configuration file in the ~/Library/Application Support/Tunnelblick/Configurations directory.
Conclusion
You should to have successfully installed and configured OpenVPN on a CentOS server after reading this guide. Additionally, you must to know how to use a client computer running Linux, Windows, or macOS to connect to the OpenVPN server.